Given the numerous requests received on the subject, with today's tutorial I decided to tell you about the techniques used by hackers to attack the computers of victims. Going into detail, I will focus on remote attacks, i.e. those that allow the bad guys to control the PCs of the bad guys remotely via the Internet.
But rest assured! In addition to showing you how to hack a PC remotely , I will also point out some solutions for everyone that allow you to effectively protect yourself from this type of threat. All you have to do is learn to recognize the "enemy", and his action techniques, and then you will see that facing him will be easier. Are you ready? Great, then I just have to wish you a good read!
Warning : accessing other people's computers without permission, and stealing the data present in them, constitutes very serious crimes. Therefore, I take no responsibility for how you will actually use the information contained in this article. It is absolutely not my intention to promote the execution of any illegal activity and, therefore, I strongly advise you not to reproduce what is disclosed.
Index
- Techniques used to hack a PC remotely
- Phishing
- Backdoor
- Keylogger
- Social engineering
- How to protect your computer from hackers
- Use common sense
- Use a good antivirus
- Run an anti-malware scan
- Configure your home router correctly
- Use a firewall
- Avoid public Wi-Fi networks
Techniques used to hack a PC remotely
Cybercriminals have various techniques at their disposal to be able to hack into a PC remotely. Those that you find indicated and explained below represent the main ones. To find out more, just keep reading the next chapters.
Phishing

Phishing is a computer scam where the hacker tries to extort sensitive data from the victim, most of the time asking them to click on links and attachments, impersonating reliable entities or people ( spoofing ) such as, for example, credit institutions, ministries, company managers, colleagues, etc.
Mostly, this type of attack happens via email. However, it is only one of several communication channels that hackers use to achieve their goal. Other channels used are SMS ( smishing ), voice calls ( vishing ) and fake websites ( search engine phishing ).
Therefore, it is advisable to pay particular attention to all e-mails you receive, not to click on attachments and links if you do not know the sender and to absolutely avoid providing any type of sensitive data.
Backdoor

One of the most popular ways to hack a remote PC are backdoors ( backdoors in Italian). This type of attack consists in building a communication bridge between the victim's computer and that of the hacker, without the victim noticing anything.
In this way, the bad guys can take control of a PC even if they are not physically present in front of the machine, making the latter perform the most varied operations (e.g. create or delete files and folders, carry other hacker attacks, etc.), without being discovered.
Backdoors are often generated through malicious software, known as trojans , which are tricked into installing on the victim's computer, making use, for example, of phishing ; or, through programs which, apparently, perform normal functions but which, in reality, operate in the background to infect the device ( trojan horse ).
They are very dangerous as they bypass the system's security functions by exploiting, where possible, the firewall ports that the user has opened to allow the operation of P2P programs (such as, for example, eMule , uTorrent and other BitTorrent programs ) and remote assistance.
Unfortunately, backdoor trojans are increasingly common, also because there are tutorials on the net that explain how to create them in a fairly simple way. For example, I myself explained to you, for illustrative purposes only, how to create a generic virus in my post focused precisely on how to create a virus .
Keylogger

Another threat to watch out for is keyloggers . You ask me what is it? I'll explain it to you right away. They are hidden software that records all the words and phrases typed on the keyboard and then sends them, unbeknownst to the user who is using the computer, via e-mail to hackers who use them to hack a PC remotely.
They are very dangerous as they allow you to trace the access passwords of Internet sites, social networks and e-mail services in a fairly simple way, as well as spy on credit card numbers and private conversations that take place on Facebook, Skype, etc.
Also in this case we are talking about quite widespread tools. I myself, purely for informational purposes, have explained to you how to do it in my tutorial dedicated to how to spy on a PC with a keylogger , even via a free keylogger .
In addition to software keyloggers , which you install like any other PC program, there are also hardware keyloggers . These are small devices that sit between the keyboard and the computer, recording everything that is typed. Unlike those of a software nature, hardware keyloggers are more difficult to find and less common.
Social engineering

Contrary to what one might believe, in order to be able to hack a PC remotely, malicious people can also act "offline" at first, making use of the so-called "social engineering" , which exploits ingenuity, inexperience and good faith of the users.
But how is this particular technique implemented? In most cases, the hacker tries to establish contact with his potential "victim" and get as much information about him as possible.
Then, after gaining his trust, if the user agrees to it, the hacker takes advantage of the situation to install some program on the victim's computer with which to remotely control the PC, as in the case of those I mentioned. talked about in my article on how to remotely connect to another PC , or to install a keylogger, as I explained to you in the previous step, so that you can then calmly monitor its activities. The installation can take place both physically and remotely.
How to protect your computer from hackers
Now that you've had the opportunity to find out what are the techniques that malicious people can usually exploit to be able to hack a PC remotely, it seems right to me to show you the tactics and resources you can use to avoid finding yourself having to face situations of this type. For more information read on, you will find everything explained below.
Use common sense

Sounds trivial, I know, but you have to believe me: the best weapon against hackers who intend to control your computer remotely is common sense .
In simple terms: avoid letting strangers or, in any case, disreputable people touch your computer, avoid downloading programs from unreliable Internet sites and clicking on dubious links. Simple but effective, have faith!
Use a good antivirus
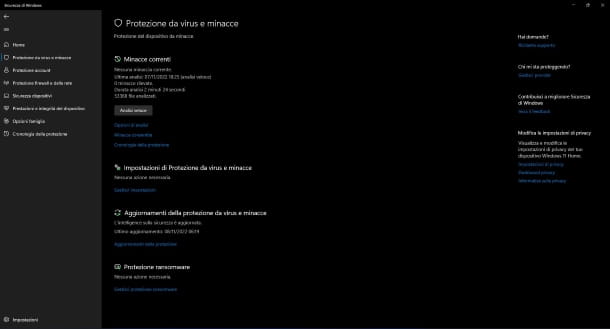
Using a good antivirus on your computer allows you to constantly monitor the system and find the presence of any computer threats. It constitutes an excellent system to preserve the PC from the action of remote hackers. With an antivirus, in fact, it is possible to find the aforementioned trojans and keyloggers (in some cases), and not only, and get rid of them instantly.
Contrary to what many may believe, among the best antiviruses out there are many free ones, including Windows Security (formerly Windows Defender ), which is included "as standard" in all the most recent versions of Windows.
By default, it is active and constantly monitors your computer. However, if you want to make sure that it is actually enabled (and, if not, proceed with activation), put into practice the instructions you find in my tutorial on how to activate Windows Defender .
If, on the other hand, you want to run a system scan now, look for Windows Security in the Start menu , click on Virus and threat protection , select the Quick scan or Full scan option from the Scan options menu to choose, in fact, whether to run a quick or complete analysis of the computer, and finally click on Start analysis .
Once the scan is complete, if threats have been identified, this will be clearly reported to you and you can eventually proceed with their removal.
If you want, you can also turn to third-party resources, such as Avira or Avast , both available in a free variant. For more information on this, I invite you to read my article on the best free anvitirus .
If, on the other hand, you decide to rely on a paid, cheap and extremely effective antivirus, I can only recommend Surfshark Antivirus which allows you to take advantage of an unlimited VPN, protect up to five devices and have advanced protection within a really light program.
On the other hand, as far as the Mac side is concerned, normally using an antivirus active in real time is not necessary, while it is advisable to run some on-demand scans from time to time.
In this regard, I recommend CleanMyMac X , an excellent all-in-one software for optimizing and securing your Mac, which allows you to free up disk space (up to 500MB for free), speed up the system by changing various settings in smart way and, what interests you more in this context, eliminate malware for macOS. I explained how to download and use it here .
Run an anti-malware scan
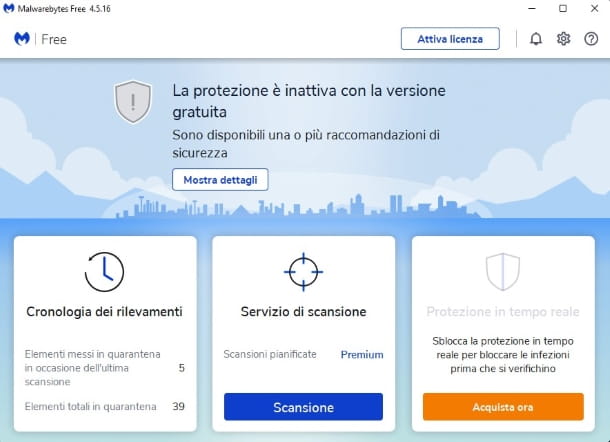
Another operation that I advise you to carry out is to equip yourself with good anti-malware software and to periodically scan the system.
In this way, you should be able to find those computer threats that the antivirus was unable to identify and / or eradicate and therefore prevent hackers from being able to control your workstation remotely using one of the aforementioned techniques.
Among the most successful anti-malware available on the market, I suggest you consider Malwarebytes Antimalware . It's hands down one of the best tools in its class, it's regularly updated to counter all the latest cyberthreats, and it's really easy to use. It can be downloaded for free but it is possibly also available in a paid variant that integrates a real-time control system (such as an antivirus).
To download it immediately to your computer, connected to the program 's download page and click on the button for the free version for Windows . When the download is complete, open the .exe file obtained and click on Yes , then on Install , then on Me and my family and Next to start the installation.
Once installed, click Complete to finish the process. At this point, after a few seconds, the program will open automatically.
Now that you see the Malwarebytes Antimalware main window on your desktop, click Get Started and then Open MalwareBytes Free . After that, click Scan to start searching for any threats.
Once the analysis procedure is finished, if any threats have been detected you simply click on the button to eradicate and/or quarantine them. Note that a system restart may also be required to complete the operation. More info here .
On Mac you can use the excellent CleanMyMac X as I explained before.
If you are looking for alternative solutions you can refer to my article on how to remove malware .
Configure your home router correctly
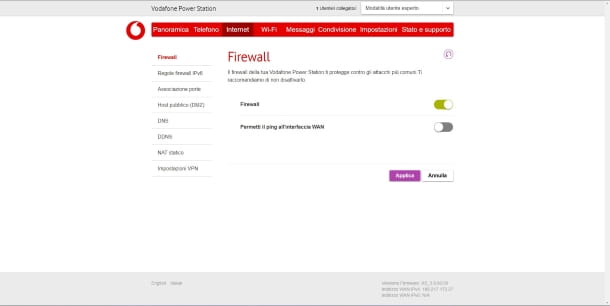
Another best practice is to strengthen the external perimeter of your network by properly configuring your router. Specifically, you need to turn on the firewall and turn off pinging the WAN interface .
The latter setting is used to prevent hackers from carrying out a DDoS attack (Distributed Denial of Service ) , a type of attack that manages to short-circuit any Internet service.
To activate your router's firewall, you must first access it. How do you say? You have no idea how to do it? Don't worry, I wrote an article just focused on how to access the router !
Once logged in, you must go to the section relating to the security settings (which can be called Security , Internet or, sometimes, directly Firewall and activate, with the relevant button, firewall protection.
If available, possibly, if it is active, you need to disable the ping setting on the WAN interface which, as explained above, will help prevent any DDoS attacks.
Use a firewall
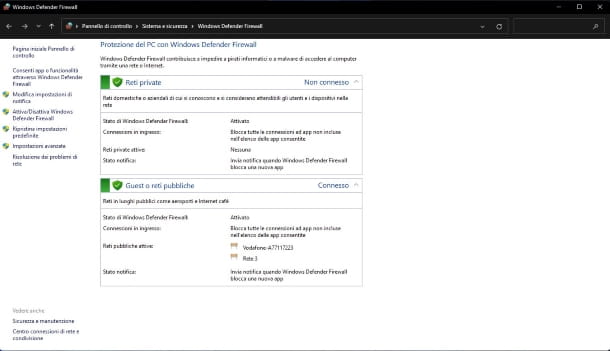
Using a firewall is another very effective way to protect your PC from hackers and various other computer threats.
If you don't know what I'm talking about, know that the firewall is nothing more than a protection system (which can be both software and hardware) placed to protect two different networks, in such a way as to prevent unauthorized access.
Windows computers integrate a firewall, called Windows Defender Firewall , which is active by default and which is able to offer a good basic level of protection.
However, you may have accidentally disabled its use. If you want to make sure of this, access the Start menu , search for and click on Windows Defender Firewall .
Now check that, in the right part of the window, in correspondence with the items Private and Guest networks or public networks there is a green shield .
If, on the other hand, there is a red shield , it means that the firewall is not active. To fix it, click on the Activate/Deactivate Windows Defender Firewall link and, in the new screen that appears, select the two options Activate Windows Defender Firewall . Then click OK at the bottom to confirm the changes.
The Mac also integrates a rather efficient firewall system. You can enable it by going to System Preferences > Security & Privacy > Firewall and then clicking on the Enable Firewall button .
If the firewall built into Windows doesn't satisfy you, you can also resort to third-party resources, as in the case of Windows Firewall Notifier and Comodo Personal Firewall .
If, on the other hand, you are looking for a valid alternative for your Mac, I suggest you try Little Snitch (for a fee) or Lulu (free and open source).
Avoid public Wi-Fi networks

Finally, I recommend that you avoid connecting to public Wi-Fi networks . You ask me for what reason? Well, simple: not being adequately protected, freely accessible wireless networks can also be used by cybercriminals to "sniff" and analyze the data of users who are connected to them.
These can then be used as a springboard for remote access. For more information, you can refer to my article on how to sniff a wireless network .
If you really need to connect to the Internet when you're not at home, I suggest you use your mobile phone as a modem, as I explained in my article on how to use your smartphone as a modem . Clearly, to do this, you must have a SIM available with an adequate data plan, especially if you plan to surf the net for several hours.
If, on the other hand, you need to connect to a public Wi-Fi network, I strongly recommend that you use it in combination with a VPN (a virtual private network) to disguise your IP, your location and encrypt all data on your connection. preventing the tracking of the latter by malicious actors and providers.
In this regard, know that there are many VPN solutions available and, if you allow me, I would like to point out a few to you: among the safest and most functional ones there are NordVPN (which I told you about in detail in this article ), Surfshark (the which information can be found in this review ), Atlas VPN (which I told you about extensively in this article ), ExpressVPN and Privado VPN (which I specifically told you about in this article ).